Authentication hell and mitigation strategies
Every day we thread a needle of authentication systems, whether it is logging in online, opening a physical door lock, making a payment…

Every day we thread a needle of authentication systems, whether it is logging in online, opening a physical door lock, making a payment, opening your garage door, or making changes to your account over call, making a judgment call managing security and ease of use. Recently I was playing around with an Electronic Hardware Hacking tool called Flipper Zero (search online if you’d like to know more about it. It’s a very versatile tool) (and yes, it does open garage doors, RFID/NFC access and TV remotes and much more!) and it sent me down this deep dive thought and discussion with my friend on security implications of everyday authentication system. All of these systems have three basic requirements that various systems try to balance and they are “Authentication”, “Security” and “Ease” and either of these can be broken into subcategories.
Authentication — Successfully verifying if the entity accessing the system has access to information they’re requesting
Security — Can the mode by which entity is verifying who they are be easily replicated by another entity into fooling the system to grant them access
Ease — Can the entity verifying the identity do so easily and without hassle
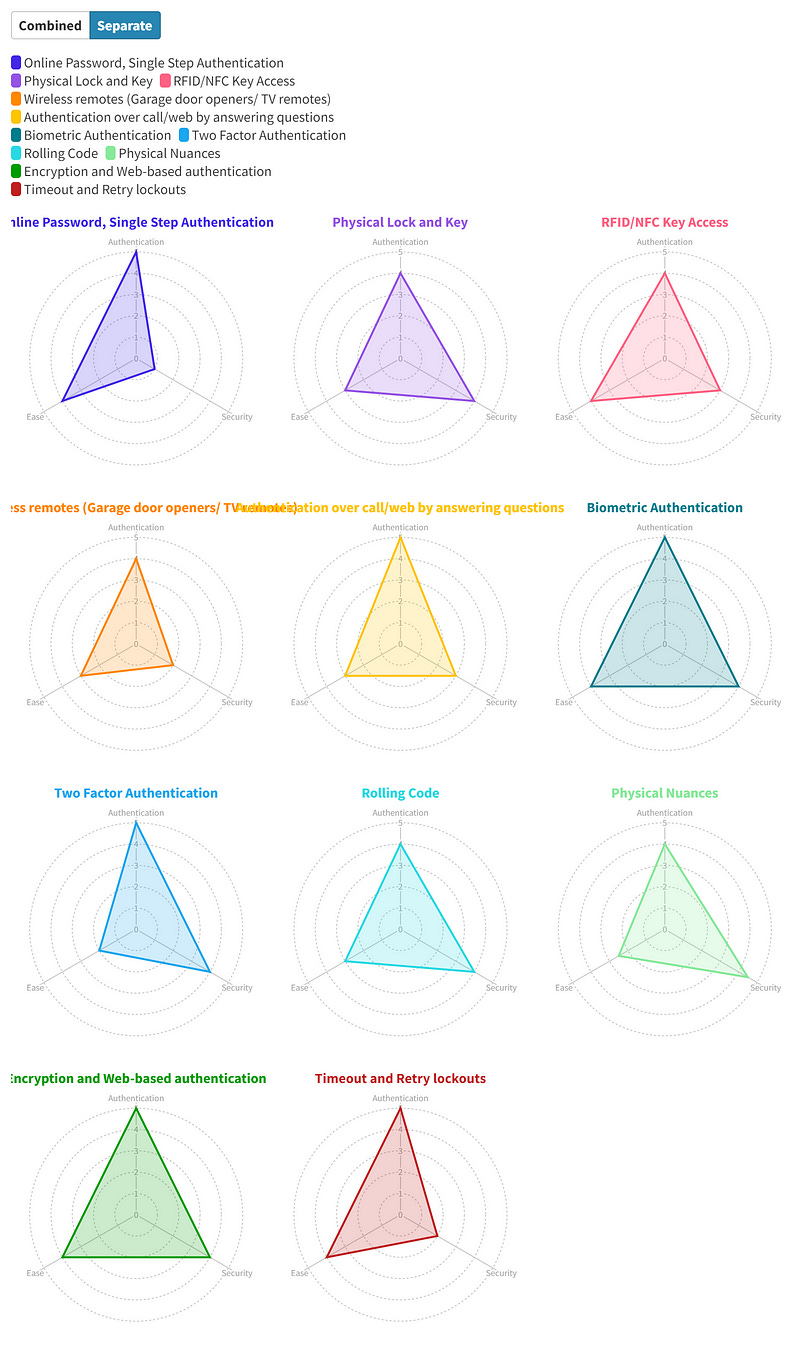
Let’s consider some examples and grade them on a scale of 1–5 for each of these

First Scenario — Online Passwords, single-step authentication
Authentication — 5 -> If the entity gives the username and password, the system can easily verify if they match or not from their records and see what kind of access they have
Security — 1-> Fooling the system is as simple as shoulder surfing, overhearing the password in the conversation, checking the browser, copying the browser cache, and many times just finding the piece of paper where the entity has written it down. Also, if someone does steal the password, there are virtually minimal ways of narrowing it down to who did it. Also, entities tend to use the same password for multiple platforms exposing them to the risk of phenomenal loss if a single password is cracked.
Ease — 4 -> Passwords are easier to remember, and can be stored in password managers or written and locked down in physical notebooks. There is also the option of “Forgot Password” for backup.
Second Scenario — Physical lock and Key
Authentication — 4 -> The system can verify if the entity has access to information but once they’re in, can’t easily limit the information they have access to.
Security — 4 -> Although not perfect, copying a physical key is a mess and needs special tools. Of course, a lock can be picked but needs special skills and tools which are not easily accessible. Stealing a key is possible but can be narrowed down based on the physical location.
Ease — 3->Keys can be carried everywhere but once the number of locks increases, it gets difficult to carry them around. Once you lose a key, you have to go through the hassle of calling a locksmith and getting a duplicate one made
Third Scenario — RFID/NFC key access
For people who don’t know how this works, the cards are generally chips that stored a password which the locking system will read once it is in its vicinity and match with the internal log to see if the entity has access to information they’re requesting.
Authentication — 4 -> Similar to physical lock and key, the system can verify if the entity has access to information but once they’re in, can’t easily limit the information they have access to. For payment systems, maybe multiple cards can have multiple spending limits but that’s around the limitation of it
Security — 3 -> Cards can be copied over and replayed by someone in a very close vicinity. With the introduction of tools like flipper zero, entry into this world is very simple and is only growing easier. Once the new entity has access to your system, it’s easier to narrow it back down to a certain extent to a physical location and possible suspects.
Ease — 4 -> Cards are easier to carry and few even can be stored in your smartphones if your smartphone supports NFC. They’re also a bit easier to replace especially if the lock is connected online.
Fourth Scenario — Wireless remotes (Garage door openers/ TV remotes)
The working of this is very similar to RFID/NFC with the core difference being now this can be operated with more distance range
Authentication —4-> Similar to RFID/NFC, all points match here
Security — 2 -> The key can be sniffed, duplicated, and replayed now by someone who is in that range and doesn’t even need to be in close vicinity. Narrowing it down becomes difficult since now the entity can be anyone in proximity, even your neighbor.
Ease — 3-> Even though one aspect i.e. things being easier to carry has become worse, there is an added comfortability of not being in the close vicinity to operate the system. Once lost, the key can generally be replaced but takes the hassle of physically getting a new one.
Fifth Scenario — Authentication over call/web by answering questions
This is generally performed in multiple ways like asking users personal questions which are on record like ID number, DoB, etc.
Authentication — 5 -> This is similar to a password verification case where the system can authenticate and limit what kind of information does the entity have access to.
Security — 3-> While being better than a password in this respect since generally there are multiple points of authentication, information can generally be overheard and noted quite easily and then replayed. It’s very difficult to track down who replayed the information once they have access to your information.
Ease — 3 -> Since there are multiple questions, all of them need to be remembered and it grows even more difficult if you’ve multiple such systems since answers would be case-sensitive and need to be written/remembered in exactly the same way. Once these answers are lost, it’s quite difficult to reset these.
Sixth Scenario — Biometric Authentication
Authentication — 5-> Same as password
Security — 4-> Very difficult to replicate and played back but is sometimes susceptible to false authentication because of noise or environmental conditions.
Ease — 4 -> Easier to access information. Sensors though growing better are susceptible to false triggers because of dirt on fingers, ambient light, etc. Difficult to reset the authentication unable to log in.
Now that we have all of these, let’s take a look at existing workarounds to handle these and a few new thought methods along with the inspiration behind those.
Two Factor Authentication
In this method, after entering the password, getting a one-time password either over SMS/email/call or via Authenticator apps or a physical USB stick with a password on it
Significantly improves security, significantly reduces ease, and is irritating.
Score
Authentication — 5, Security — 4, Ease — 2
Rolling Code
Usually found in wireless remotes. Instead of one password, remotes send different passwords each time and each password can only be used once and hence prevents someone from sniffing and replaying attacks.
Significantly improves security without affecting Ease
Score
Authentication — 4, Security — 4, Ease — 3
Physical Nuances
While not a deliberate method, I’ve seen this method work better by increasing security and very minorly decreasing ease. For physical lock and key, in this case, because of either aging or manufacturing defects, the key only works at a certain angle or by pressing the lock in a certain way. The abusing entity even if they get access to the key, won’t know this method which is known only by regular users hence adding more security.
Score
Authentication — 4, Security — 4.5, Ease — 2.5
Encryption and Web-based authentication
Increase the security while slightly decreasing the ease. Significantly increases the complexity of verifying the system.
Score
Authentication — 5, Security — 4, Ease — 4
Timeout and Retry lockouts
This prevents entities to infinitely try and brute force the passwords
Score
Authentication — 5, Security — 2, Ease — 4
Possible new workarounds and security measures implementation
Taking inspiration from various above methods and certain novel ideas arising from discussion and brainstorming, below we discuss a few of those.
Algorithmic passwords
This works by making an internal personal algorithm to generate passwords. For example, taking a phrase, then the platform name or information available on the login page, and merging it to generate a password. This increases the security considerably seeing that even if one password is cracked, the abusive entity doesn’t have access to all platforms. It also doesn’t compromise much on ease. e.g. of this would be login into gmail can be “here1sgoogleMail” and login for Instagram can be “here1sInsta”
Extending Algorithmic Passwords to dumb electronic devices
The same concept can now be extended to another method like wireless authentication. The lock system shares timely data, the key actually processes this data with some algorithm and sends back the password. If it matches internal calculation, the entity is authenticated, else they’re not. This prevents someone from sniffing the password and replaying it and the key will be changing each time someone uses the system or in a timely/algorithmic manner.
Wherever there is an electronic system, we run into the risk of easily copying/ sniffing/ replaying data. So, now it’s possible someone can read the complete algorithm in the controller's memory directly and replicate it in their hardware. Though difficult, it is possible.
Adding Randomness
One interesting research I came across recently to tackle this was, using the manufacturing imperfections implicit in the Silicon chip manufacturing process in order to generate a random key unique to each chip and incorporating it in the algorithm for password generation. Since this will be unique to each chip, it makes it virtually impossible for someone to copy it.
System Access Notifications
Another additional method would be to add 3rd party systems which tell the entity once the system is accessed. This won’t prevent abusive entities from entering the system but can take quick action to narrow down abusive entities and lock down on access. These will be approaches like adding real-time notifications when someone accesses your system, adding security cameras, sensors, etc.
Concluding: If you made it here, here is a certificate of perseverance. Would love to hear your thoughts. Remember, these security risks only have to go wrong once. Better take suitable precautions. Having said that, also have to manage the ease. Yes, we can have the best security system but is it worth having to spend minutes of inconvenience/ irritation each time you log in? Also, is my stuff really worth taking such efforts? Those are some questions to which each individual will have different answers to and that is what will determine someone’s partial fate.
Credits and References
Flipper Zero — The device that triggered the chain of thought. Visit them at — https://flipperzero.one/

Tanmay Band: The dude who entertained the discussion by adding endless points.
flourish.studio: Platform to create easy visualization. Try it out at — https://flourish.studio/
